This page provides specific information about how authentication and authorization work in CXone Mpower. If this is the first time you've worked with these concepts, you should gain a basic understanding of authentication and authorization ideas and terminology first.
Once you've reviewed this material, you're ready to:
- Set Up CXone Mpower Authentication Using the Built-in Identity Provider
- Set Up CXone Mpower Authentication Using an External Identity Provider
When users log in to any application suite, including CXone Mpower, these two steps typically occur in the order shown:
- Authentication—Is the user who they claim to be?
- Authorization—Should the authenticated user have the access they've requested?
All users must be authenticated and authorized before they can access CXone Mpower.
Users can be people or applications. For example, chatbots and virtual assistants often run by means of a user account. Most application suites use the same processes for human and virtual users. In these online help pages about authentication and authorization, we've used the term user to apply to both people and applications. If there are differences, they're clearly explained.
Authentication can be complicated to set up and difficult to test and validate. To set up authentication in CXone Mpower, you need to understand:
-
How authentication works in CXone Mpower
-
The built-in CXone Mpower identity provider
-
External identity providers
-
Differences between authenticating human users and application users
You also need to know how authorization works in the CXone Mpower platform.
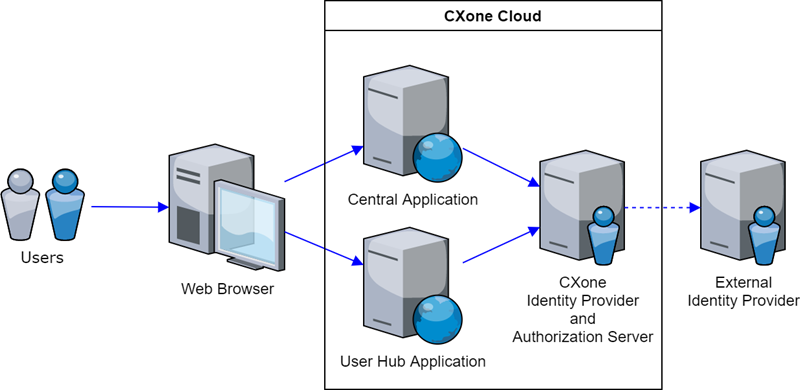
This illustration shows how CXone Mpower authenticates and authorizes users:
-
A user accesses CXone Mpower through a supported web browser.
-
CXone Mpower asks for the user's login credentials.
-
The user provides credentials.
-
CXone Mpower verifies them with an identity provider (IdP). CXone Mpower has its own built-in IdP, but it can also work with an external IdP.
-
Once the user is authenticated, the CXone Mpower Authorization Server provides access to the CXone Mpower platform. CXone Mpower does not support external authorization systems.
Authentication Using the Built-In Identity Provider
The built-in CXone Mpower IdP authenticates users with a username and password. Each username must be unique to your organization. You can optionally add multi-factor authentication (MFA) for an additional security layer.
Application Users
Sometimes applications need access to CXone Mpower features and functionality. CXone Mpower treats these applications, like bots and interactive virtual assistants (IVAs), as users. Application users are only supported with built-in authentication. In addition, application users don't use login authenticators. Instead, they use access keys.
User Login with Built-In Authentication
Users first see a screen that asks for their username. Until CXone Mpower knows the username, it cannot ask for additional credentials. CXone Mpower can only ask for passwords or MFA tokens once it knows which user is logging in.
After the user enters their username and clicks NEXT, a new window asks for the user's password. Once the user enters their correct password and clicks Sign In, CXone Mpower authenticates the user and grants them access to the system.
This window looks slightly different for
Password Management with Built-in Authentication
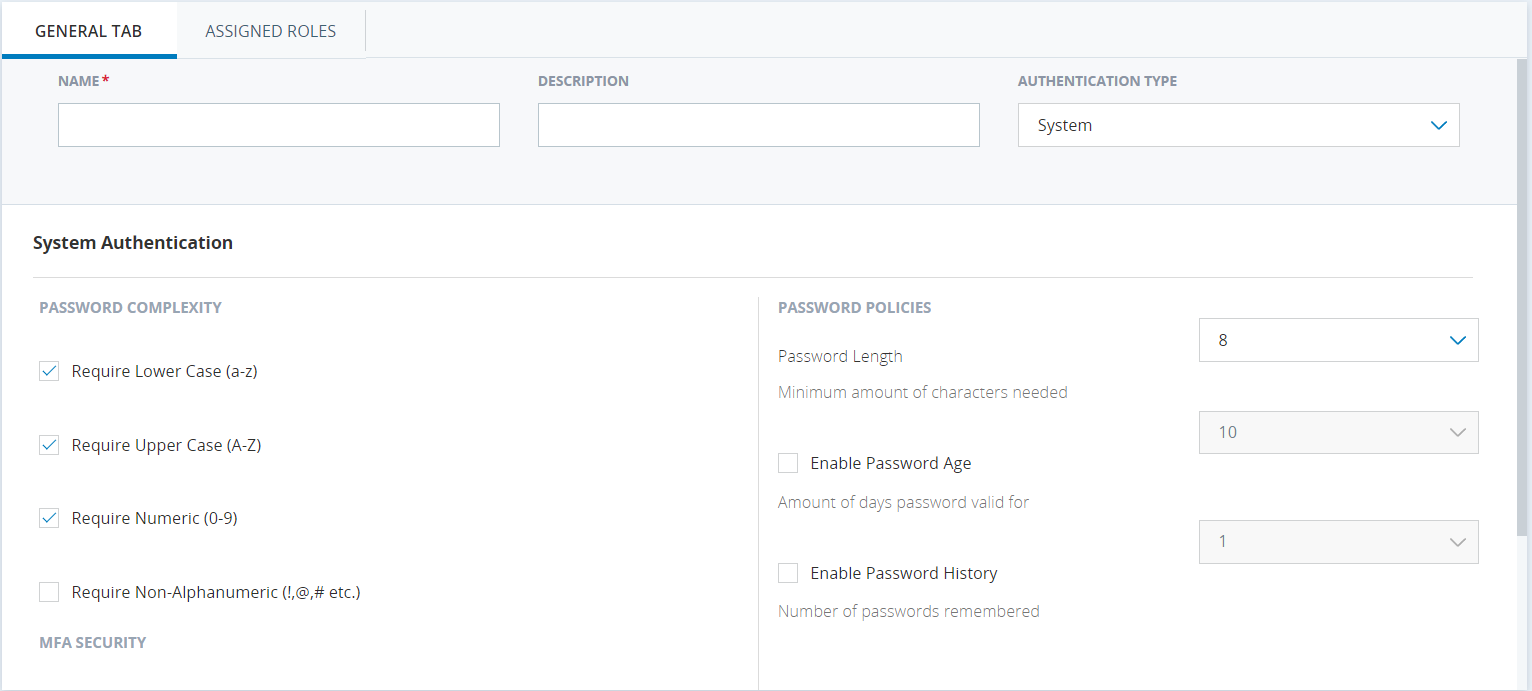
Password criteria can be customized with login authenticators. With a login authenticator, you can control:
-
Number of characters required in a password
-
Types of characters required in a password
-
Number of days before the user has to reset their password
-
Number of wrong password attempts allowed before the account is locked
-
Number of passwords that CXone Mpower remembers, which prevents users from reusing those passwords
Passwords are not visible in CXone Mpower. For privacy and security, passwords are maintained internally and can only be changed using a forgot password or resent password flow. Users can use the link on the password login screen and follow the on-screen instructions. Users will receive an email notifying them if their password has been changed.
CXone Mpower comes with a default login authenticator you can use if you don't need custom login authenticators. You still must assign this default authenticator to the
You can set up as many custom login authenticators as you'd like. For example, you can require more complex passwords for users that have access to valuable information. Any time you want to make an authentication requirement different for a user account, you'll need to create a new login authenticator. Changes to authenticators apply to assigned users the next time they log in.
You can also set up multi-factor authentication (MFA) with custom login authenticators. MFA increases your security by adding another layer of authentication. For example, you could have your users authenticate with a username and password. Then, you could have them authenticate again with a code sent to their mobile devices. These codes are typically known as MFA tokens, even when a physical token is not involved.
CXone Mpower supports both major types of MFA:
- Time-based—typically used by software authenticators like Google
- Counter-based—typically used by hardware tokens
You can enable MFA for login authenticators with a single checkbox. However, the specific information about users, their MFA settings, and their identities is maintained in the individual employee account.
Login authenticators are assigned to roles. This means an employee's authentication method depends on the role they are assigned.
Authentication Using an External Identity Provider
When you sign in to a system with an account from another site, you're using external authentication. For example, you might log in to an app on your phone with your Google account.
External authentication, sometimes called federation, uses an external identity provider (IdP) to help authenticate users. The external IdP works with the CXone Mpower IdP to authenticate the user. To work together, both IdPs rely on authentication protocols.
External IdPs
CXone Mpower supports both hosted and cloud service identity providers.
You should be familiar with your identity provider. If not, work with your company team that manages authentication. Setting up federation can be difficult if the right people are not involved. Your organization may have established processes for integrating systems like CXone Mpower with your identity provider. Following these processes and meeting your specific security needs is your responsibility. The NiCE team for CXone Mpower is here to support you along the way.
Authentication Protocols
IdP-initiated flows apply to single applications, not the entire CXone Mpower suite. For example, you can use this flow to launch the main user interface applications, but you cannot use it to launch other applications like Studio. For the entire suite to function seamlessly, the SP-initiated flow is required.
Authentication protocols establish communication and trust between different IdPs. CXone Mpower supports an authentication protocol called SAML 2.0.
SAML 2.0 is an established technology and is widely used than newer technologies like OpenID Connect. It supports service provider (SP)-initiated authentication flow. This is a familiar flow and the model used by many apps and websites. The user experience is:
- Users enter their credentials in CXone Mpower (that is, they log in).
- CXone Mpower uses its built-in IdP to communicate with your external IdP to verify the user identity.
- CXone Mpower uses its built-in authorization to verify the authenticated user's access levels.
- CXone Mpower provides correct access to the authenticated, authorized user.
SAML 2.0 also supports a less-common IdP-initiated flow. In this flow, your user enters their credentials with your IdP. Then, the IdP launches CXone Mpower.
For SAML 2.0, CXone Mpower only supports signing the Message/Response, not the Assertion.
Your users may be familiar with either or both of these authentication flows. If you use SAML 2.0, be aware of the limitations presented by each flow. These are discussed more in the next section.
CXone Mpower does not support additional encryption offered by some authentication protocols.
Evaluate the Combination
The CXone Mpower suite does not support every combination of application, external IdP, and authentication protocol. In some cases, support doesn't exist. In other cases, there are limitations with workarounds. It's difficult to show potential issues for every combination and scenario, so you should do a test setup with your identity provider. Your test should take into account your different use cases and user flows. The following table can help guide your evaluation.
| CXone Mpower Application | External IDP | Authentication Protocol | Limitations and workarounds |
|---|---|---|---|
| CXone Mpower Platform and All Applications | All | All | Does not support encryption of claims. |
| CXone Mpower Platform and All Applications | All | SAML 2.0 | Only message signing is supported. Public certificate must be included in the response. |
| CXone Mpower Platform | All | OpenID Connect | Not supported. |
Only the main web applications support the IdP-initiated SAML 2.0 flow. Users who need access to Studio or the various agent applications must use built-in authentication or an SP-initiated flow.
Establish Trust
Identity providers must trust each other before they can communicate. Each provider must have information about the other. What information is required depends on the authentication protocol. How the information is obtained depends on the IdP.
There are several configuration parameters used to establish trust with SAML 2.0. Work with your Account Representative to use these parameters to create a trusted relationship between your CXone Mpower tenant![]() High-level organizational grouping used to manage technical support, billing, and global settings for your CXone Mpower system. and your external IdP.
High-level organizational grouping used to manage technical support, billing, and global settings for your CXone Mpower system. and your external IdP.
|
Field |
Details |
|---|---|
| Entity ID |
A pre-populated, non-editable global unique ID that your external IdP may require you to enter on their side when using the SAML 2.0 protocol. The IdP includes it as the entity ID of the issuer in the SAML 2.0 request message. Some IdPs, including Okta and OneLogin, don't require you to configure the entity ID on their side. Others, including Salesforce, do. |
|
Endpoint URL |
The endpoint URL provided by your IdP. |
| Assertion URL |
A pre-populated, non-editable URL your IdP requires to set up any SAML 2.0 flow. It serves as an endpoint URL for receiving and parsing an authentication assertion. You must enter this ID in your IdP configuration, usually in the ACS URL field. Some IdPs call it something other than ACS. For example, in the Okta SAML 2.0 template, you enter this URL in the Single Sign On URL field. |
| Certificate | Your IdP will provide you with a security certificate. |
Authentication of Applications
Users and applications are authenticated in very similar ways. The main difference is that applications are authenticated with an access key while users are authenticated with a username and password. Unlike users, applications are not required to interact through a browser. They can function in a back-office environment.
You can create
Authorization in CXone Mpower
Authorization is the process of verifying what resources a user is allowed to access. Resources can include applications, files, and data. You can define users' access to resources with
A user's authentication method doesn't impact authorization. CXone Mpower uses the same authorization process for all users. It doesn't matter whether they are authenticated with access keys or passwords.