This topic provides guidelines for configuring Avaya TSAPI interface with DMCC for CXone Mpower Real-Time Third Party Telephony Recording (Multi-ACD).
The supported Avaya AES TSAPI versions are 8.1.3, 10.1, 10.2.
Avaya site engineer is responsible for all procedures in the Avaya environment. The procedures described in this section are by recommendation only!
Follow these steps to set up the Avaya TSAPI interface with DMCC.
Step 1: Prepare Avaya AES TSAPI Environment
Step 2: Prepare Avaya AES DMCC Environment
Step 3: (Optional) Configure the additional integration:
Step 4: Download and save the Essential Data for 3rd Party Connectivity Config in CXone Mpower Excel file. You will be required to fill in essential information as you proceed. Once you have finished entering all the necessary details and prepared your environment for Real-Time Third Party Telephony Recording (Multi-ACD), you must submit the Excel file to your NICE Professional Services representative.
Prepare Avaya AES TSAPI Environment
You must configure the Avaya AES TSAPI Server before you configure Real-Time Third Party Telephony Recording (Multi-ACD).
The supported Avaya AES TSAPI versions are 8.1.3, 10.1, 10.2.
Perform these steps to prepare the Avaya AES TSAPI environment:
Step 1: Verify the TSAPI License and Status
Step 2: Prepare the AES Environment
Step 5: Create a Secure Connection Using VPN
Step 1: Verify the TSAPI License and Status
Before configuring the Avaya TSAPI interface, you must verify that the Avaya TSAPI Service is running, and that the license is valid.
To verify the TSAPI Service and status:
-
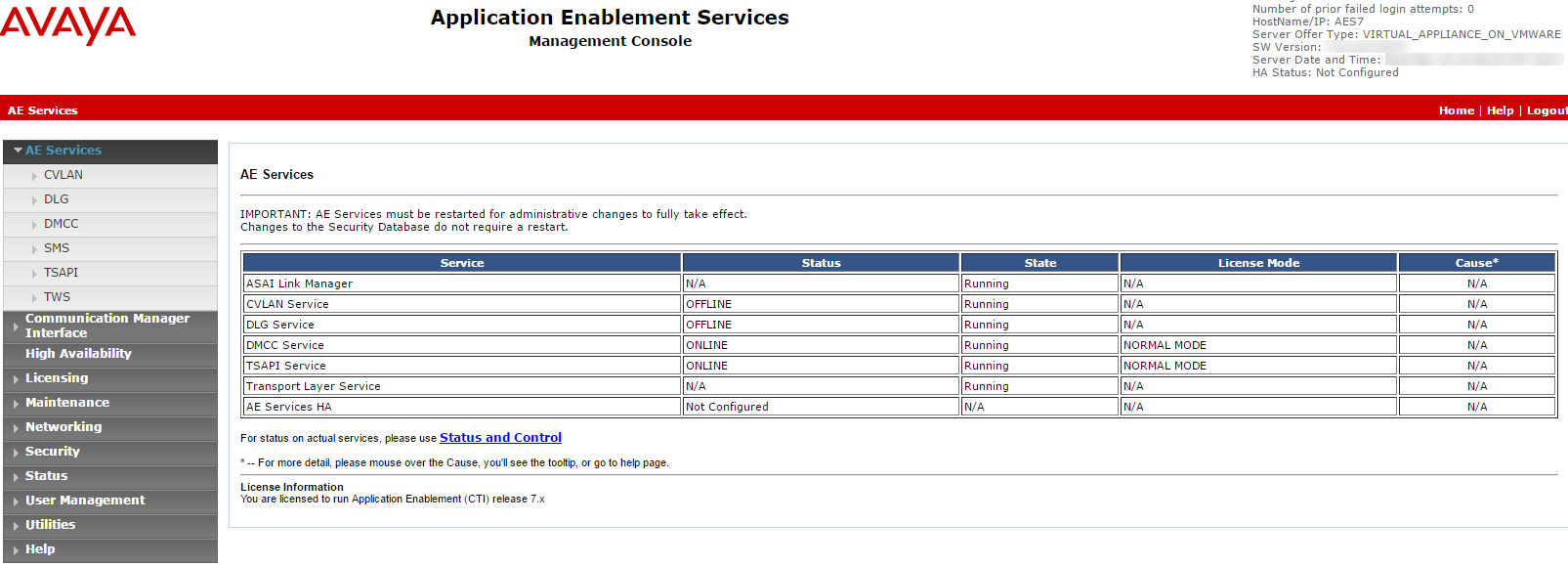
Log in to the AES Server. The Application Enablement Services page appears.
-
From the menu, select AE Services.
-
Verify:
-
The TSAPI Service Status column is Online and that the State is Running.
-
The Licensed Mode column shows Normal Mode.
-
Step 2: Prepare the AES Environment
An Avaya site engineer is responsible for all procedures in the Avaya environment. These procedures are recommendations and guidelines only!
In an AES environment, the AES administrator must prepare the AES-CTI link connections.
To configure the switch on the AES (general guidelines):
-
Navigate to the AES webpage and login.
-
Enter your Username and Password. Click Login. The Home page appears.
-
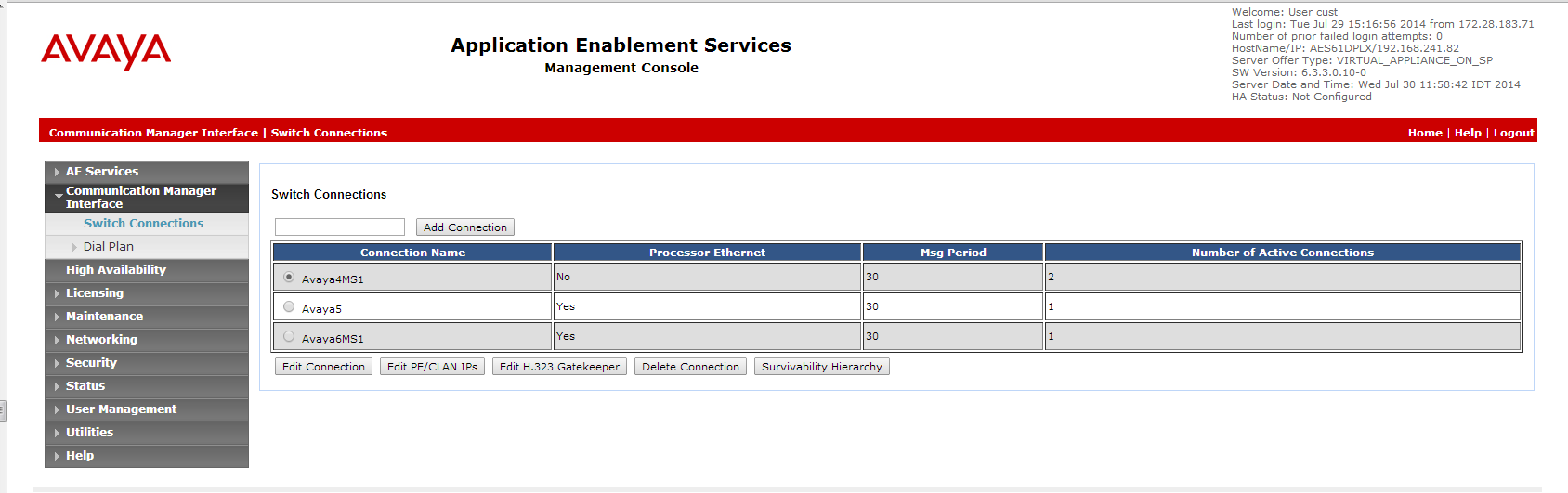
From the menu, click Communication Manager Interface.
-
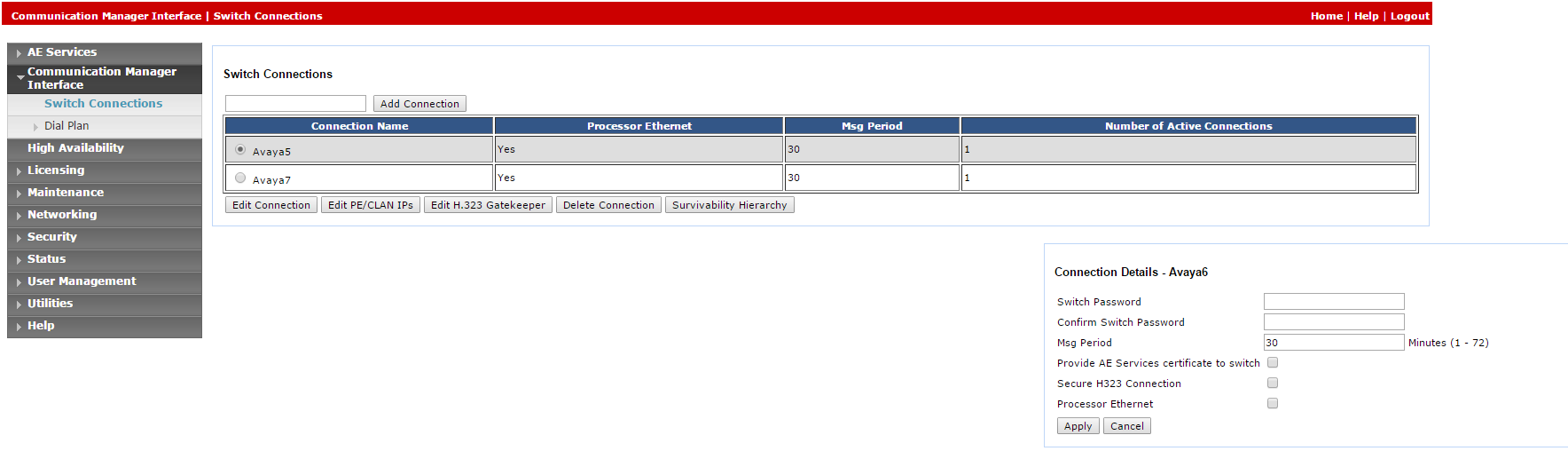
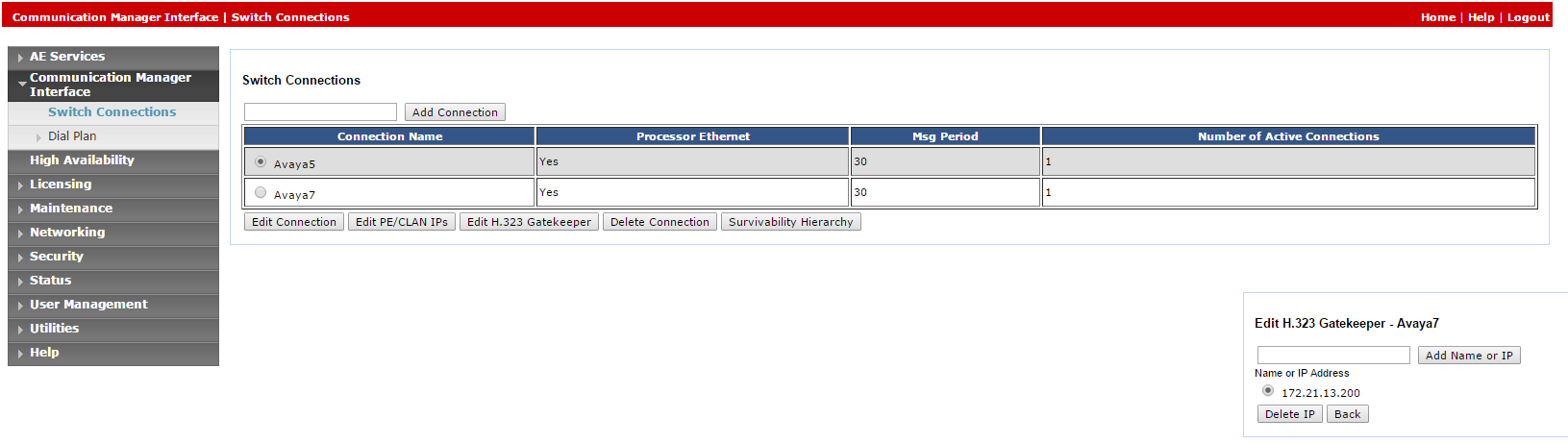
Select Switch Connections.
-
In the Switch Connections window, in the field add the switch name and click Add Connection. The Connection Details window for the new switch appears.
-
In the Switch Password field, enter the switch password. The switch password must be between 12 - 16 alphanumeric characters and identical to the password assigned to the AES service in the Communication Manager.
-
In the Confirm Switch Password field, enter the switch password again.
-
If your Communication Manager supports Processor Ethernet, select Processor Ethernet.
-
Click Apply. The Switch Connections window reappears.
-
-
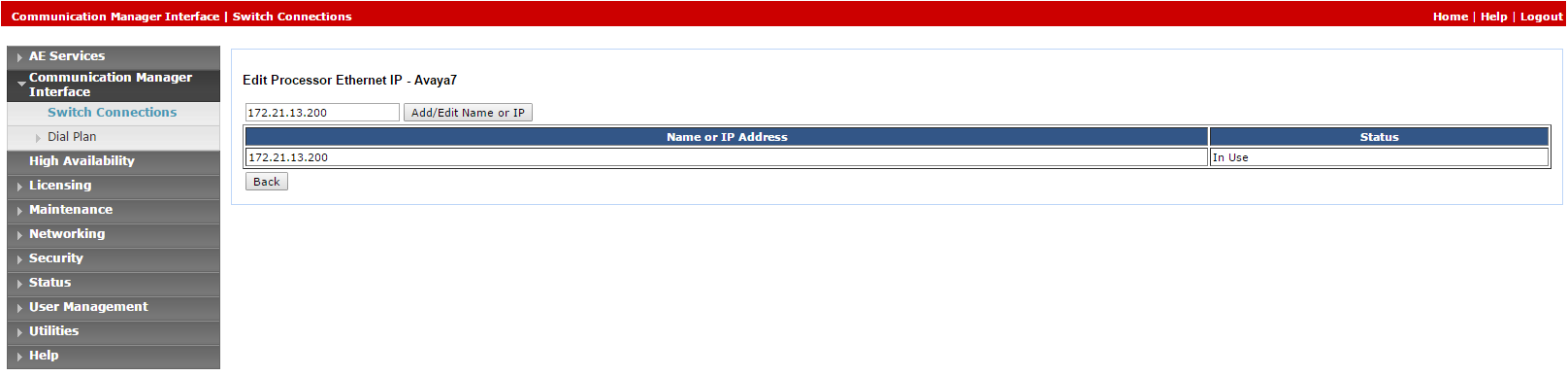
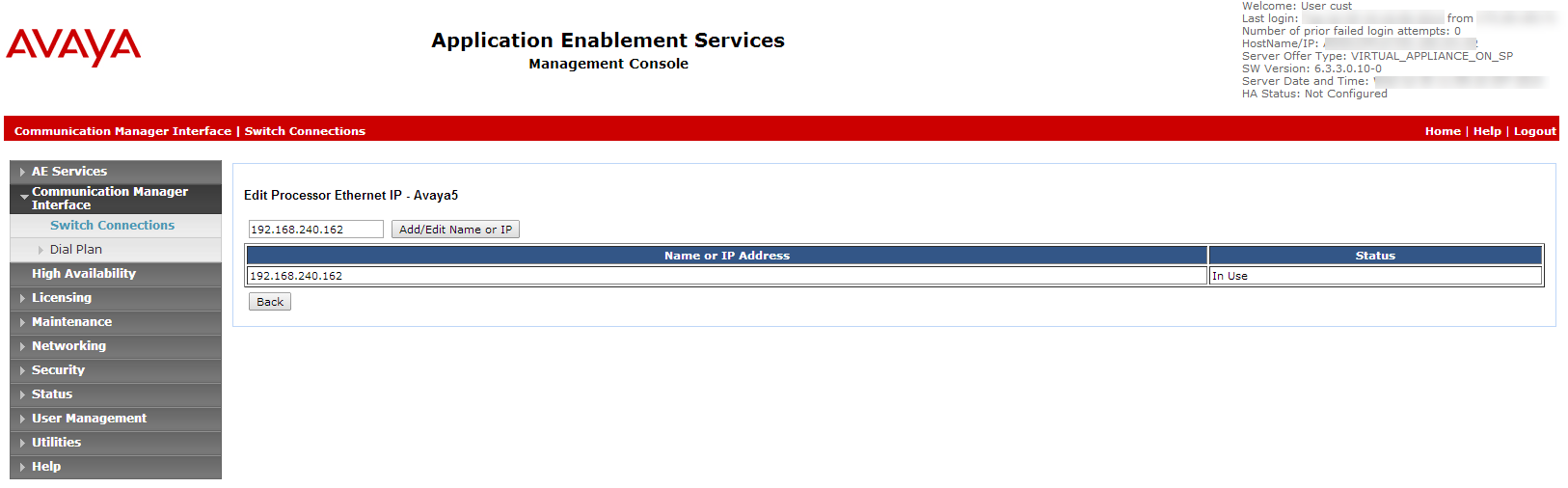
Click Edit PE/CLAN IPs. The Edit Processor Ethernet IP window appears.
-
In the field provided, add the IP address of the Processor Ethernet/CLAN board, then click Add/Edit Name or IP.
-
In the AES menu, click Switch Connections to return to the Switch Connections window.
-
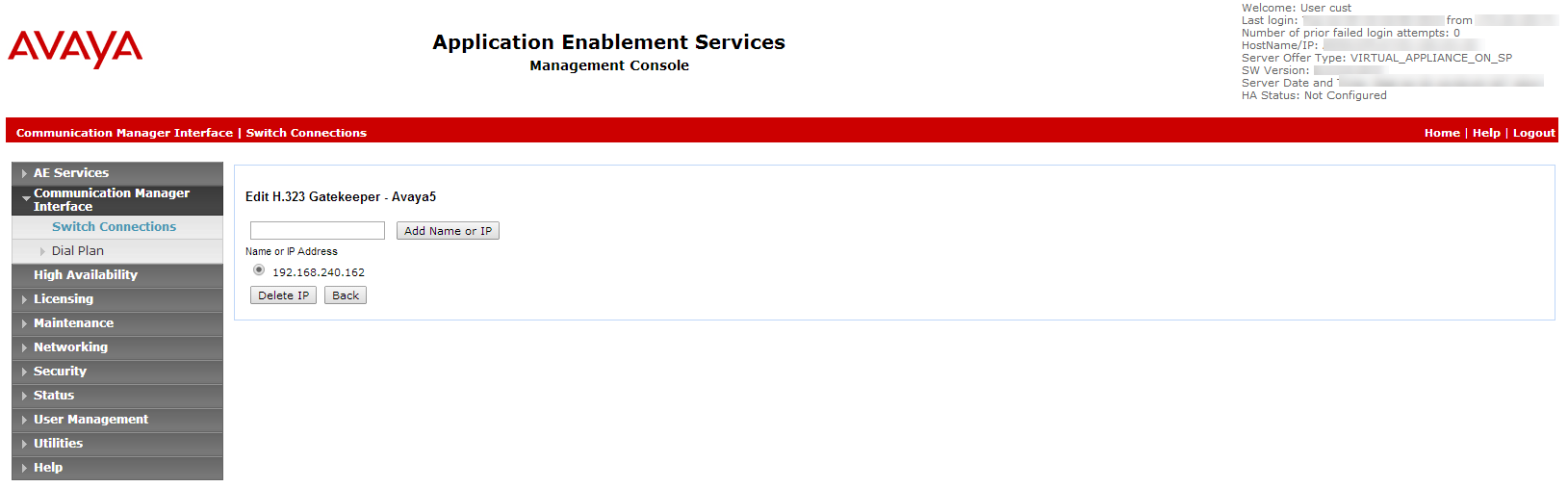
Click Edit H.323 Gatekeeper. The Edit H.323 Gatekeeper window appears.
-
In the field provided, enter the IP address of one of the Processor Ethernet/CLAN boards, and click Add Name or IP. Repeat this step for all Processor Ethernet/CLAN boards.
After the CTI link is configured, the administrator should verify that the AES-CTI link connection is active and in a Talking state.
To verify the CTI link:
-
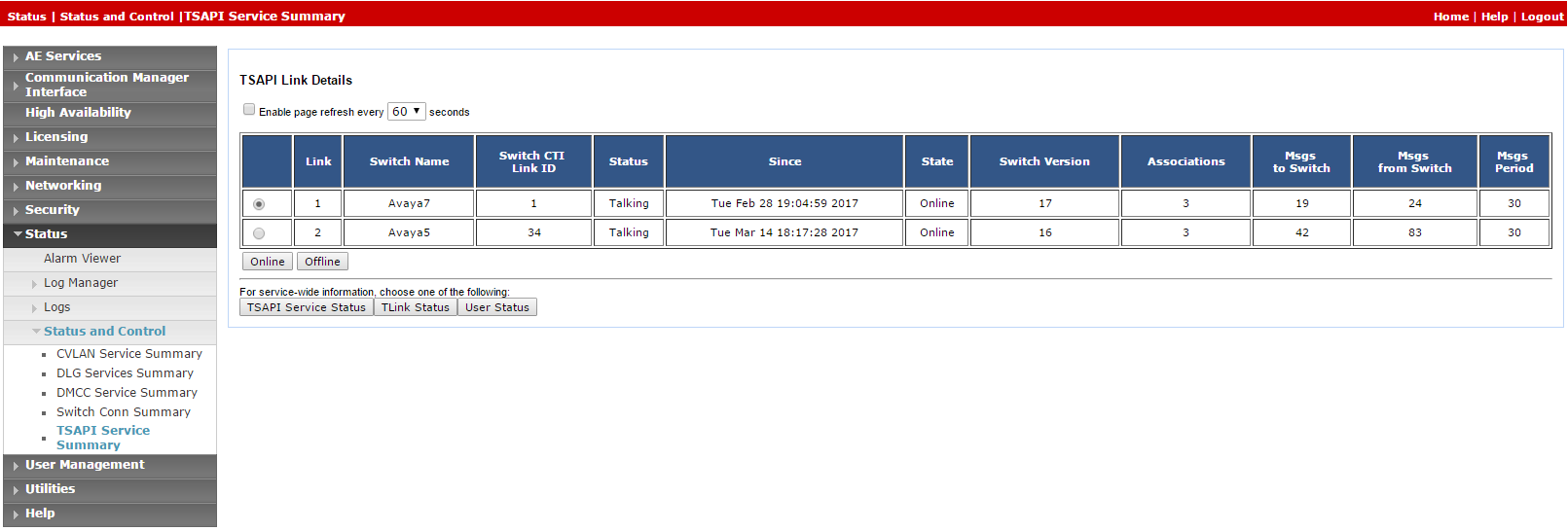
From the AES webpage, select Status > Status and Control > TSAPI Service Summary.
-
Check the Status is set for Talking for the relevant AES-CTI link connection.
Step 3: Add a User
The user must be added to the system via the webpage.
This procedure must be performed together with an Avaya administrator. The AES administrator must first prepare the AES-CTI link connection.
At the end of this step, you are required to provide to NiCE Professional Services:
-
User credentials.
To add a user:
-
On the AE Services menu, navigate to User Management > User Admin and click Add User.
-
In the Add User window, configure the mandatory fields:
-
User Id
-
Common Name
-
Surname
-
User Password
-
Confirm Password
-
Change the CT User setting to Yes.
-
-
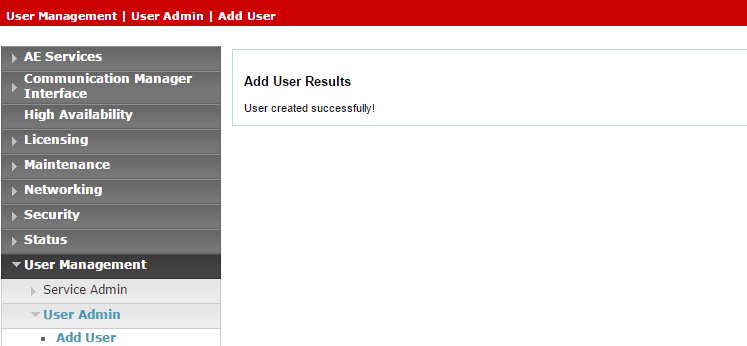
Click Apply to save the information.
-
Save these user credentials in the Excel file. Once you have finished entering all the necessary details and prepared your environment, submit the Excel file to NiCE Professional Services.
-
Verify that the User created successfully message appears in the Add User Results window.
-
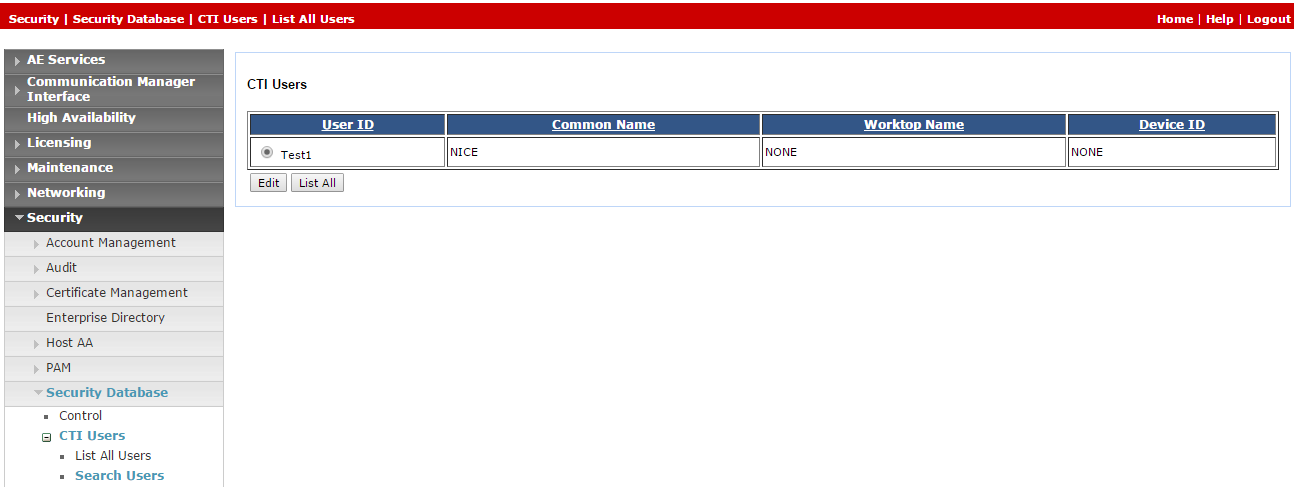
Provide unrestricted monitoring for all devices to user:
-
On the AE Services menu, expand Security > Security Database > CTI Users and click Search Users.
-
In the Search Users window, search for the user created previously.
-
Click Search. The new user appears.
-
Click Edit.
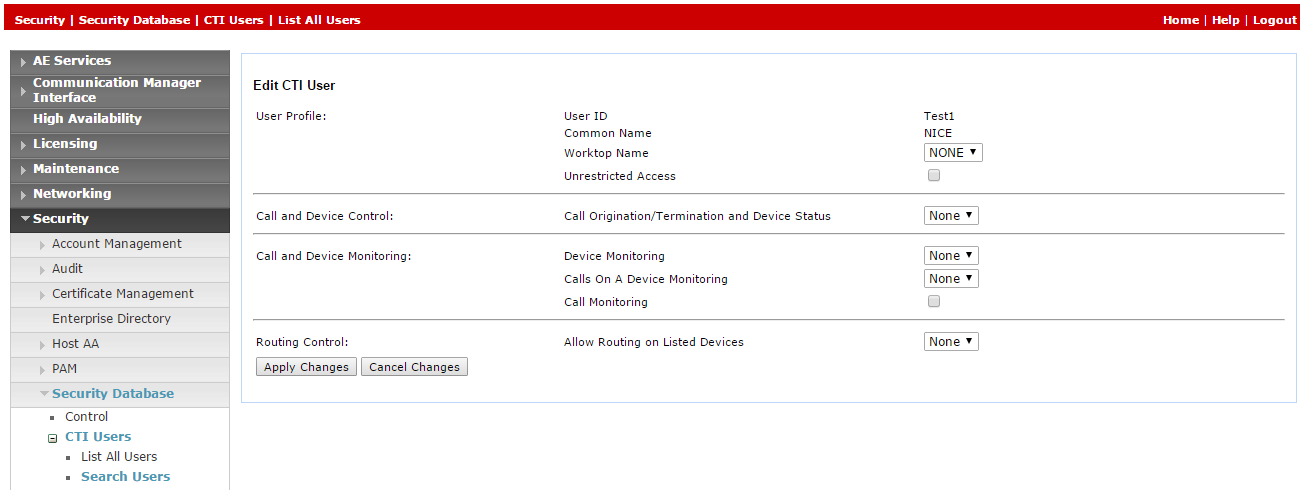
-
In the Edit CTI User window, in the User Profile area, select Unrestricted Access.
-
Click Apply Changes.
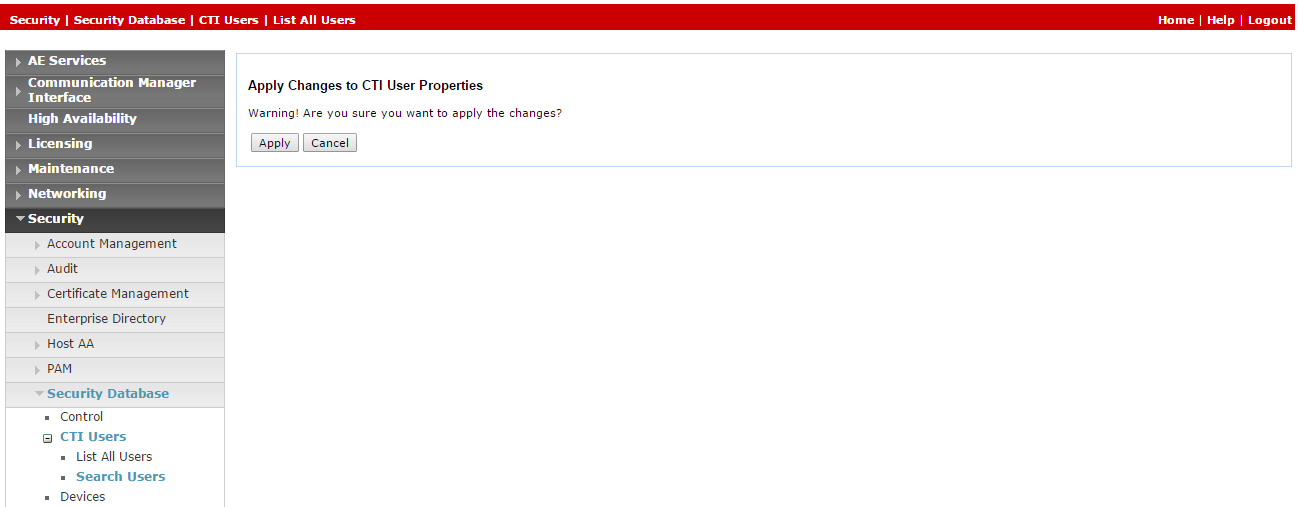
-
In the Apply Changes to CTI User Properties, click Apply.
-
Step 4: Verify the Tlink
In the CTI Connection TSAPI configuration, the Server Name parameter uses the Tlink value.
At the end of this step, you are required to provide to NiCE Professional Services:
-
Tlink name
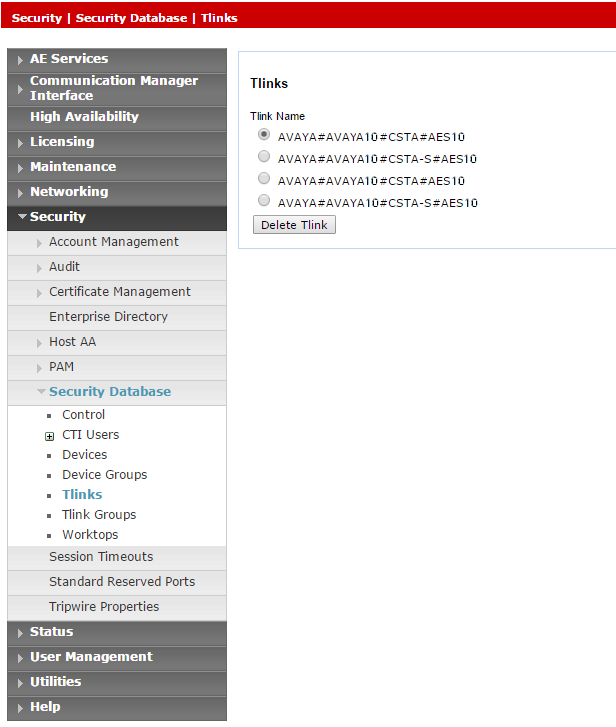
To verify the Tlink:
-
In the AES webpage, select Security > Security Database > Tlinks.
The list of Tlinks appears in the Tlink Name column. If your site uses more than one Tlink, make sure you choose the correct Tlink, according to the switch name.
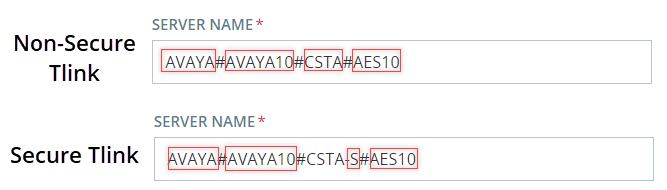
The Tlink consists of these segments:
-
AVAYA - Vendor
-
# - Separator
-
AVAYA10 - Switch / Connection Name (as defined in Communication Manager Interface> Switch Connections)
-
CSTA/CSTA-S - Non-Secure / Secure Portal
-
AES10 - AES Server Name
-
-
Save the correct Tlink name in the Excel file. Once you have finished entering all the necessary details and prepared your environment, submit the Excel file to NiCE Professional Services.
-
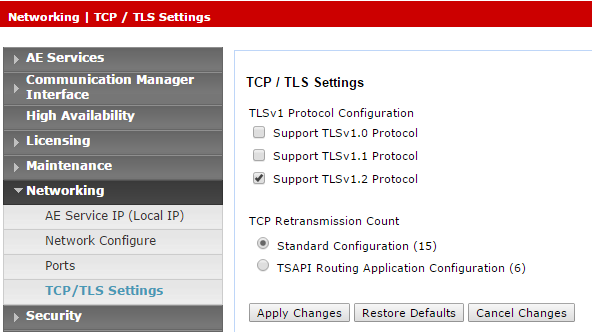
If using the secured Tlink, verify that the TLS version is configured in the AES. Navigate to Networking > TCP/TLS Settings.
-
By default, only Support TLSv1.2 Protocol is enabled. TLSv1.2 Protocol is supported as a sole security protocol.
-
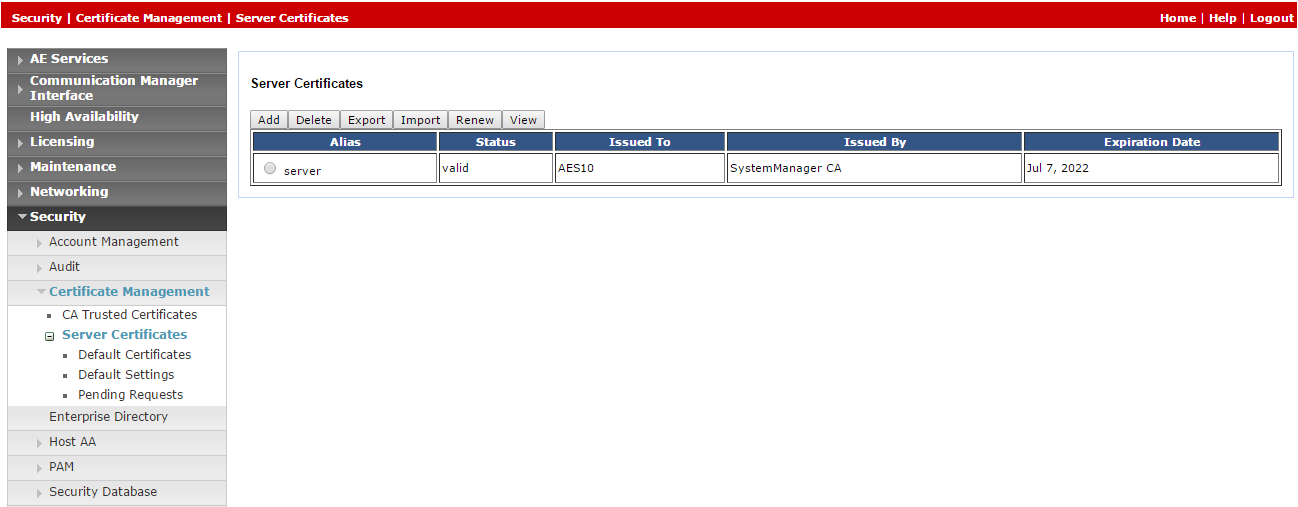
Since default certificates are no longer provided, the Avaya site engineer must generate the relevant certificate and upload it to the Avaya telephony system in CXone Mpower. Navigate to Security > Certificate Management > Server Certificates.
-
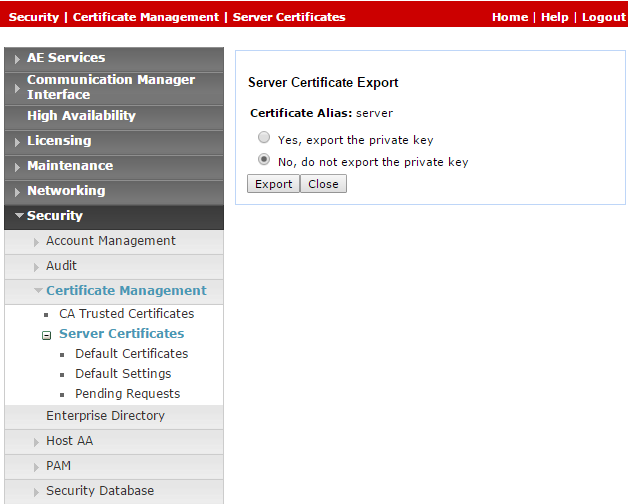
In the Server Certificates window, in the Alias column, select the certificate and click Export.
-
In the Server Certificate Export window, verify that No, do not export the private key is selected and click Export.
-
Upload this exported certificate to the Avaya telephony system in CXone Mpower.
Step 5: Create a Secure Connection Using VPN
This step must be performed only in coordination with NiCE Professional Services.
At the end this step, by completing the form in the Essential Data for 3rd Party Connectivity Config in CXone Mpower Excel file, you will provide the necessary details to NiCE Professional Services, who will aid you in establishing a secure VPN connection with CXone Mpower.
SIPREC environments only are required to complete additional information in the form, so that SBC can establish a connection between SIPREC and CXone Mpower.
-
NiCE Professional Services will provide you with the VPN connect form.
-
Fill out the provided form with details of your side and the necessary information for Real-Time Third Party Telephony Recording (Multi-ACD).
-
NiCE Professional Services will coordinate with CXone Mpower teams to ensure all fields are appropriately filled out.
-
Both parties must agree on the form and details.
-
-
NiCE Professional Services will schedule a collaborative call:
- To agree on the form and provided details with Real-Time Third Party Telephony Recording (Multi-ACD).
-
With CXone Mpower teams for VPN provisioning.
-
You will set up two VPNs: one for resiliency and one for failover.
-
Configure routing by setting up BGP over VPN with Real-Time Third Party Telephony Recording (Multi-ACD) firewalls or create static routes to the provided IP addresses.
-
Configure NAT. NAT your endpoint behind a public IP, either advertised via BGP or using static routing.
-
Configure firewall settings:
-
Allow inbound traffic from the provided IP addresses (2) into the CTI Endpoint.
-
Open the required ports. See Ports and Protocols by Application for more information.
-
For High Availability environments, the ports mentioned above in step b must be open for all servers, active and standby.
-
-
NiCE Professional Services will coordinate with CXone Mpower teams to:
-
Ensure the VPN form is correctly filled out.
-
Schedule a time with CXone Mpower teams for VPN provisioning and routing setup.
-
Test VPN tunnel, routing, and connectivity.
-
Prepare Avaya AES DMCC Environment
This section describes how to prepare the Avaya Device Media Call Control (DMCC) environment for Real-Time Third Party Telephony Recording (Multi-ACD).
The supported Avaya AES DMCC versions are 8.1.3, 10.1, and 10.2.
Avaya site engineer is responsible for all procedures in the Avaya environment. The procedures described in this section are by recommendation only!
For comprehensive information about configuring the Avaya switch, see the Avaya documentation.
Workflow
Use this workflow to set up Avaya DMCC active recording with Real-Time Third Party Telephony Recording (Multi-ACD).
Before beginning this workflow, you must ensure that site components are configured.
Step 1: Configure Virtual Extensions to Capture Audio
Step 2: Configure SRTP
Step 3: Optional: Configure Two DMCC Observers on a Single Tenant
Step 4: Prepare information for NiCE Professional Services
Before You Begin
Before integrating the Avaya DMCC environment with Multi-ACD (Open), gather the required information and enter it in the Essential Data for 3rd Party Connectivity Config in CXone Mpower Excel file you downloaded. Once you have finished entering all the necessary details and prepared your environment, submit the Excel file to NiCE Professional Services.
Configure Virtual Extensions to Capture Audio
Use these procedures to prepare the Avaya Communication Manager for a site using virtual extensions for audio capture.
When using virtual extensions to capture your audio, verify you have enough licenses for the NiCE CTI.
-
Log in to the AES Server. The Application Enablement Services page appears.
-
From the menu, select Licensing > WebLM Server Access.
-
Log in to WebLM Server.
-
Select Licensed products > Application Enablement from the panel on the left, and verify that sufficient licenses are defined for DMCC DMC.
Before the DMCC Server can register the emulated (virtual) extensions on the Media Gateway, define the extensions on the switch.
Each virtual extension must be separately defined and requires a DMCC license. Make sure the total number of DMCC licenses match the maximum number of agents operating concurrently. However, it is recommended to maintain DMCC licenses at least 20% above the maximum call volume.
When your site is configured for Single Step Conference, you must define the virtual extensions on the AES in the same group as the extensions observed via Single Step Conference. Otherwise, the user will be granted unrestricted access to the security database.
To define the virtual extensions for recording on the switch:
-
On the switch, open a console window and type this:
-
Extension Type: 4624
ExtensionType 4624 represents all soft phones.
-
IP Softphone: Y (Yes)
-
Security Code: This is the password for the extension. It will be used in the Device Password field when configuring the Avaya DMCC interface under Third Party Telephony in CXone Mpower. The Security Code must be consistent for all virtual extensions.
-
The Avaya AES Server supports up to 16 simultaneous C-LAN connections. This allows the AES Server to provide load balancing across multiple connections and a C-LAN failover mechanism.
You configure the symbolic name, or Connection Name, on the Avaya AES Server. The symbolic name represents multiple C-LANs on the Avaya Media Gateways. This allows the recording system to implement redundancy and load sharing over multiple C-LANs by communicating with the symbolic name. Multiple C-LANs are required in implementations of over 300 Avaya DMCC channels.
The symbolic name is the Connection Name on the AES, and is case sensitive.
To configure the symbolic name:
-
From the AES webpage, select Communication Manager Interface > Switch Connections.
-
Select the required Connection Name and click Edit PE/CLAN IPs.
-
Enter the host name or IP address of the C-LAN or/and PE for AES connectivity, and then click Add/Edit Name or IP. Repeat for each C-LAN or PE attached to this connection.
-
In the Switch Connections window, click Edit H.323 Gatekeeper.
To use the symbolic name feature, the H.323 gatekeeper must be specified. The C-LAN configuration alone is not sufficient. The H.323 IP list can be different from the C-LAN IP list.
-
Select the required Name or IP Address, or type in the host name or IP address of the H.323 Gatekeeper and click Add Name or IP.
-
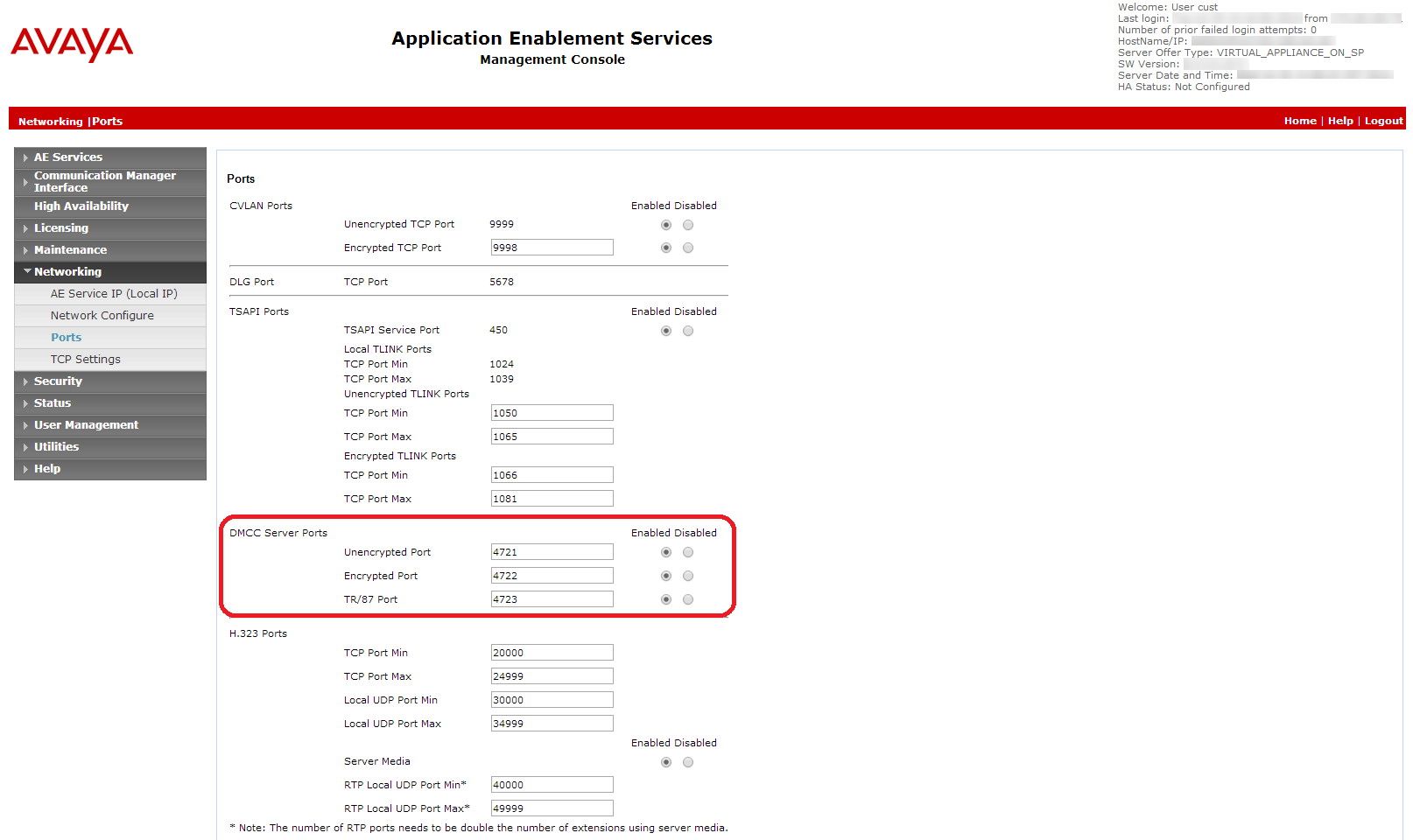
Select Networking > Ports.
-
Ensure that the DMCC Server port is enabled.
The codec set defined in Real-Time Third Party Telephony Recording (Multi-ACD) must match the codec set defined on the switch.
-
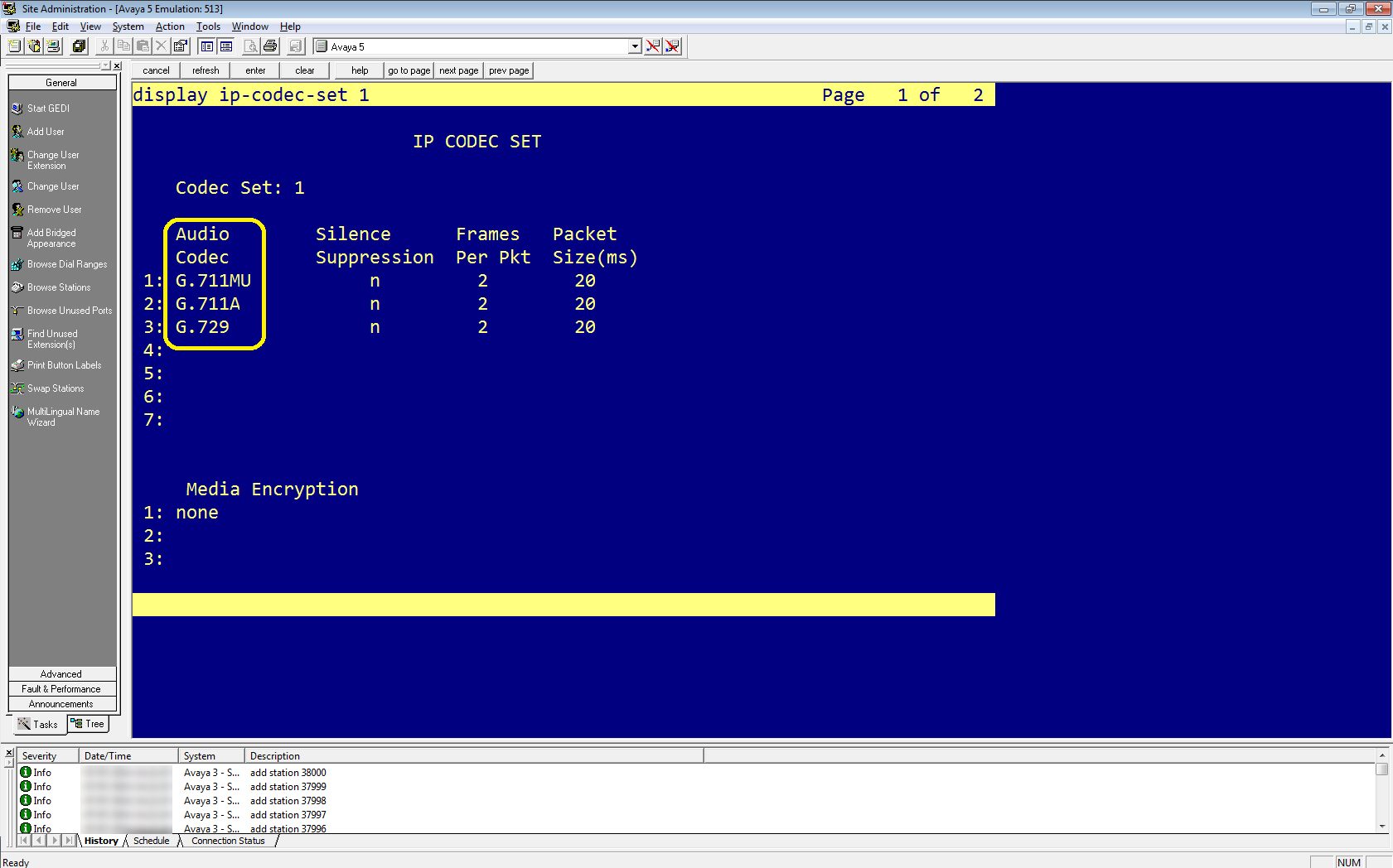
In Avaya Site Administration, enter display ip-codec-set <n> where <n> is the codec set associated with the IP network region of the extensions that you need to observe.
-
In the Audio Codec column, review the list of compression types. These are the codecs that the switch allows.
Make sure that the CodecList you define in Real-Time Third Party Telephony Recording (Multi-ACD) contains at least one of the compression types defined here.
-
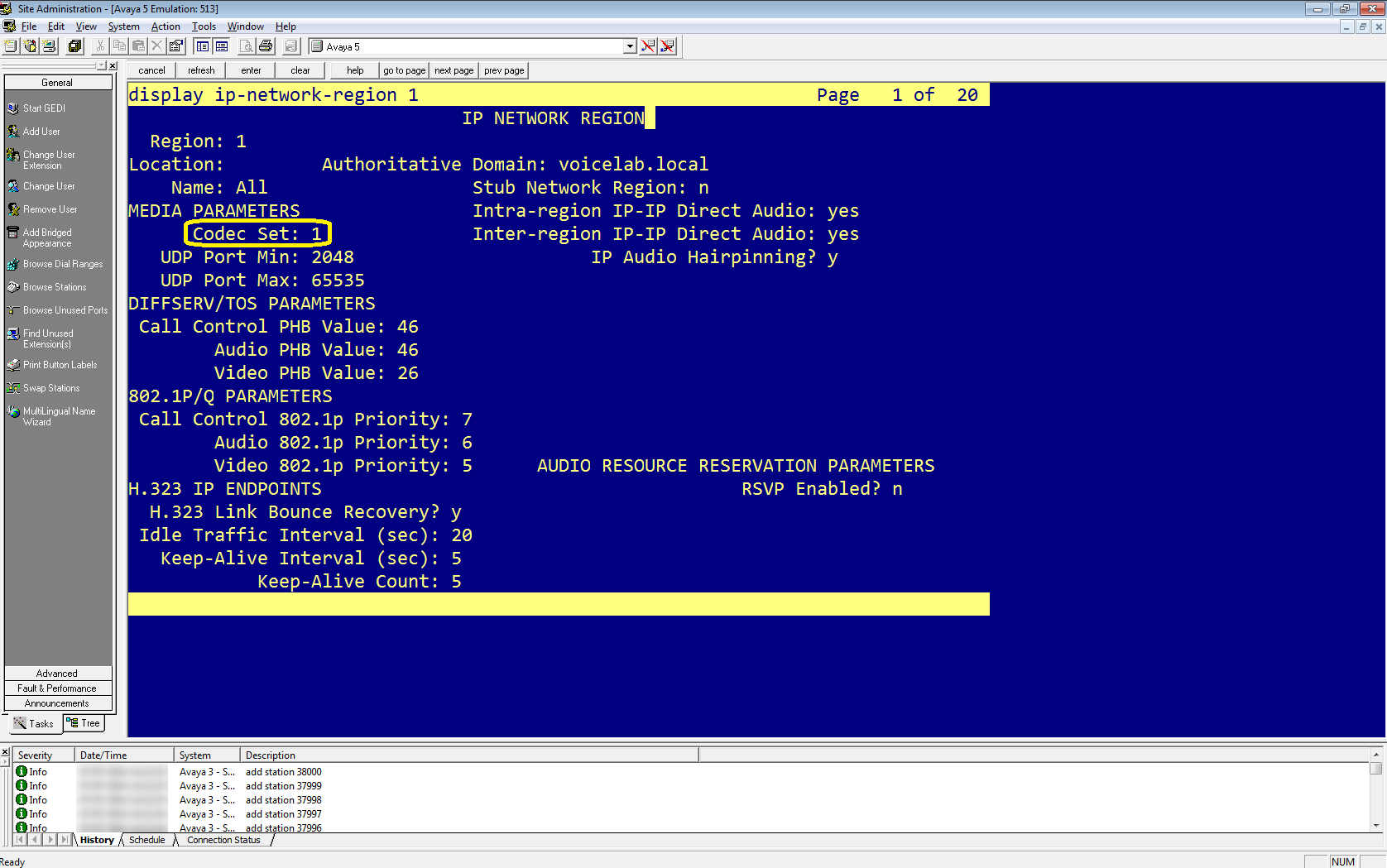
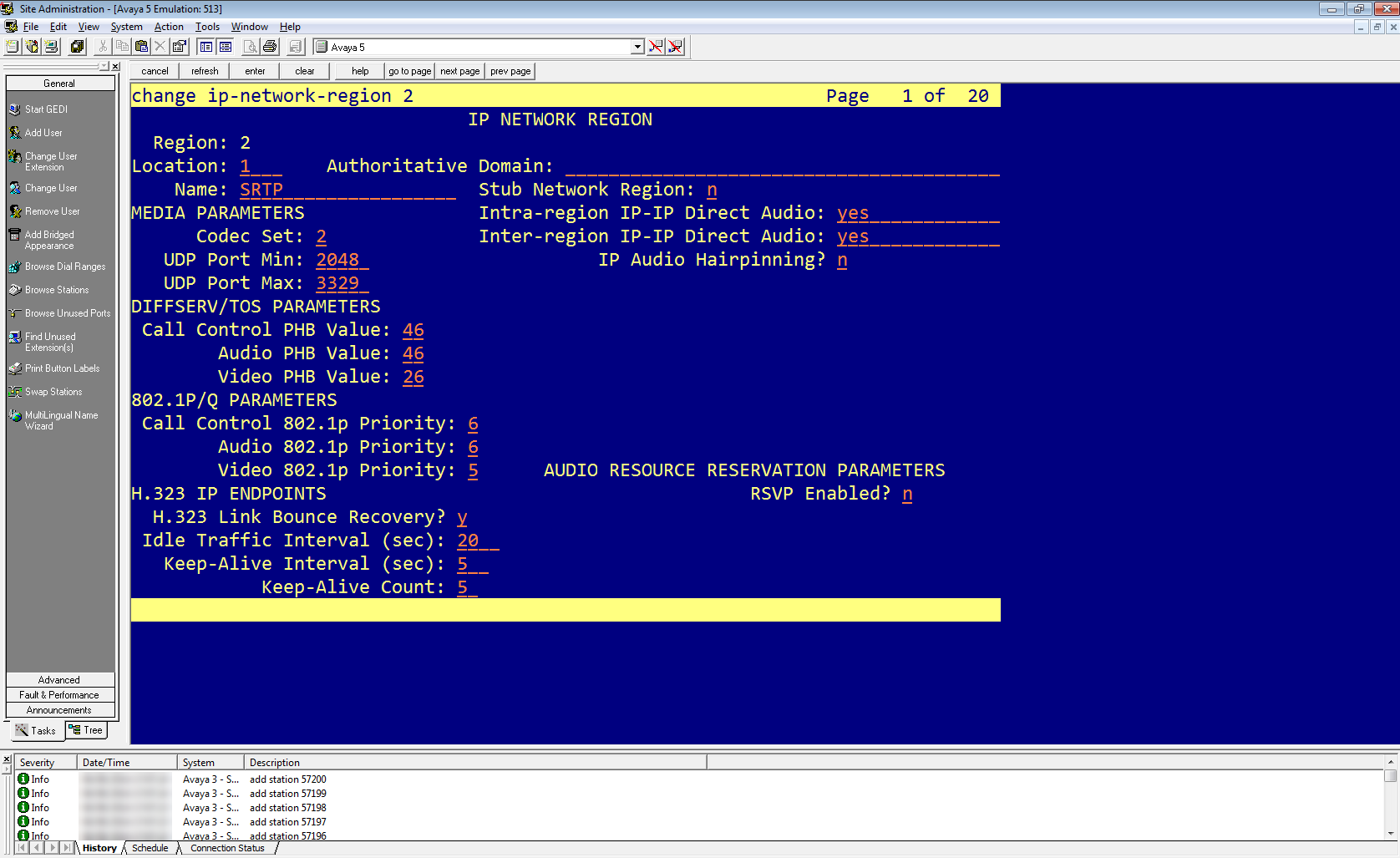
Enter display ip-network-region <n> where <n> is the network region of the extensions that you need to observe.
-
Verify that the defined Codec Set is the ip-codec-set you confirmed above.
Verify that the silence suppression feature is enabled on Avaya Media Server for audio codecs. This conserves bandwidth by not transmitting audio packets during periods of silence. Silence suppression may cause audio clipping.
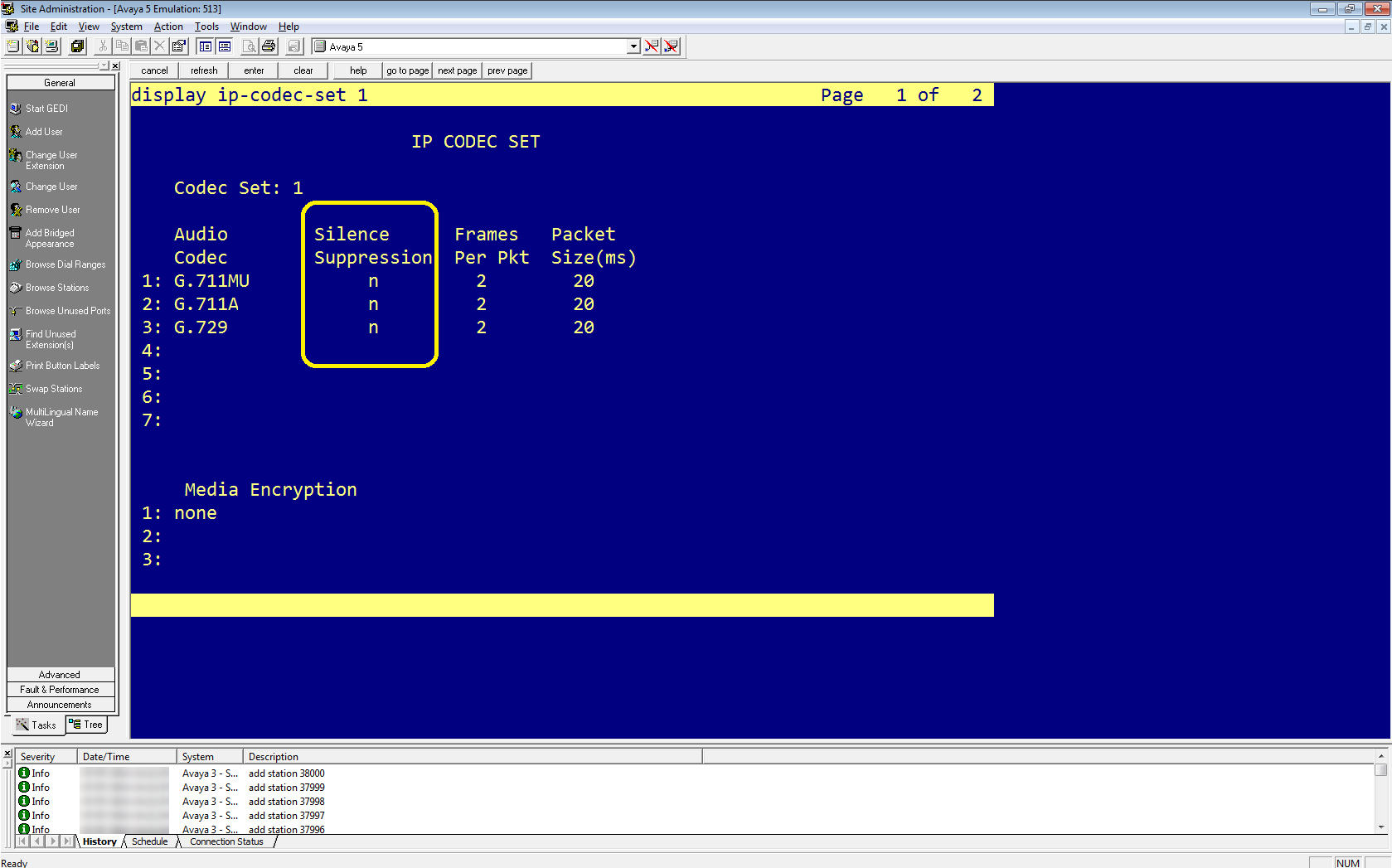
-
In Avaya Site Administration, enter the display ip-codec-set <n> command, where <n> is the number of the codec set associated with the IP network region of the extensions that you need to observe.
-
In the IP Codec Set window, in the Codec Set section, for each codec listed you can set in the Silence Suppression column:
-
Enable silence suppression, define Silence Suppression as y.
-
Disable silence suppression, define Silence Suppression as n.
-
-
Press Esc and then e to submit your changes.
Configure SRTP
Use these procedures when your site requires SRTP configuration.
-
Log in to the Avaya Aura Media server.
-
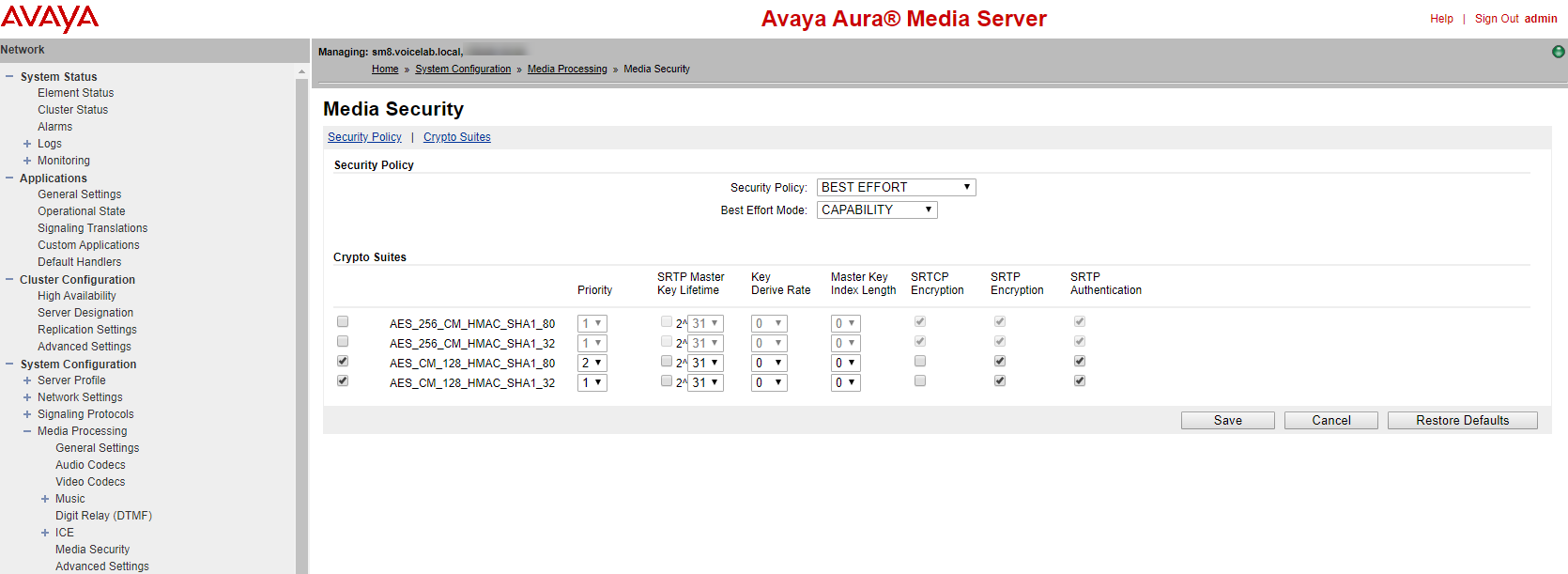
Under the System Configuration menu, go to Media Processing > Media Security.
-
Verify that:
-
Security Policy is set to BEST EFFORT.
-
Best Effort Mode is set to CAPABILITY.
-
-
Under Crypto Suites, enable:
-
AES_CM_128_HMAC_SHA1_80
-
AES_CM_128_HMAC_SHA1_32
-
-
For each of them, select SRTP encryption and SRTP Authentication.
-
Go to Configuring Avaya Switch Encryption for the IP Network Region.
SRTP encryption is configured on two levels: the signaling (H.323) and the media stream (SRTP).
This section describes how to enable SRTP and signaling encryption on Avaya Communication Manager.
At the end of this procedure, you are required to provide to NiCE Professional Services:
-
Encryption used on site: HMAC32 or HMAC80.
To configure encryption:
-
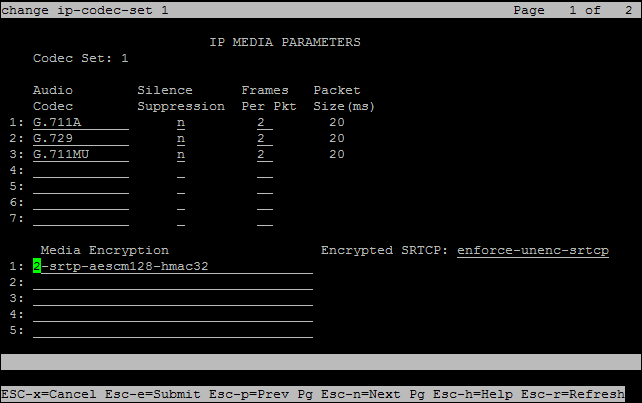
In Avaya Site Administration, enter the display ip-codec-set <n> command, where <n> is the codec-set associated with the IP network region of the extensions that you need to observe.
-
Verify if the site has:
-
Avaya Media Servers with G Series gateway/s. aes can be supported only with G-series gateways.
-
Avaya Media Servers, use either 2-srtp-aescm128-hmac32 or 1-srtp-aescm128-hmac80.
-
-
In the IP Codec Set screen, in the Media Encryption section, enter one or more of the Media Encryption types.
-
2-srtp-aescm128-hmac32
-
1-srtp-aescm128-hmac80
-
aes - not supported if using Avaya Media Server
The Avaya site engineer must inform NiCE Professional Services which encryption is used on site: HMAC32 or HMAC80.
Save the encryption information in the Excel file. Once you have finished entering all the necessary details and prepared your environment, submit the Excel file to NiCE Professional Services.
-
-
In Avaya Site Administration, enter the display ip-network-region <n> command, where <n> is the network region of the extensions that you need to observe.
-
In the network region, enter the IP Codec Set you edited previously.
-
When you configure CLAN/Medpro: In the Network Region, enter the region you configured for encryption. In the example in this procedure, to enable SRTP in the Network Region, enter 2.
Optional: Configure Two DMCC Observers on a Single Tenant
CXone Mpower supports using two DMCC Observers in one tenant![]() High-level organizational grouping used to manage technical support, billing, and global settings for your CXone Mpower system.. Use this setup when you need greater scalability or redundancy across two separate Avaya systems.
High-level organizational grouping used to manage technical support, billing, and global settings for your CXone Mpower system.. Use this setup when you need greater scalability or redundancy across two separate Avaya systems.
To support two DMCC Observers on a single CXone Mpower tenant, the environment must be modeled as two fully independent Avaya telephony systems:
-
Telephony System A
-
AES Server A connected to Communication Manager A (CM A)
-
Dedicated virtual extension range (VE Set A)
-
-
Telephony System B
-
AES Server B connected to Communication Manager B (CM B)
-
Dedicated virtual extension range (VE Set B)
-
Both systems must use different AES servers, different Communication Managers, and non‑overlapping DMCC virtual extension ranges. Each AES server may use local HA (Active–Standby).
-
Complete all steps required to prepare the Avaya AES DMCC environment for a single telephony system.
-
Make sure that you have:
-
Two independent Communication Managers (CM A and CM B)
-
Two AES servers (AES A and AES B) with:
-
Valid DMCC licenses
-
CTI user and Tlink
-
DMCC ports enabled (secure or non-secure or both)
-
-
Two unique virtual extension ranges (one per telephony system)
-
-
Verify that network or security teams or both are ready to configure:
-
VPN and routing to both AES servers
-
SBC settings for both Observers
-
DNS (for example, Route 53) for Observer FQDNs
-
For each AES/CM pair, NiCE Professional Services will set up two matching Avaya DMCC telephony entries in CXone Mpower.
Run the Prepare Avaya AES DMCC Environment workflow twice, once for each telephony system, with these constraints:
-
Configure AES A and AES B independently:
-
Separate Tlinks (one per AES).
-
Separate CTI users (or distinct credentials) if required by your security policy.
-
Verify DMCC ports on each AES (secure and/or non-secure).
-
-
Define the Virtual Extensions for Recording:
-
On CM A, create a VE range dedicated to Telephony System A.
-
On CM B, create a separate VE range dedicated to Telephony System B.
-
Do not reuse the same VE numbers between CM A and CM B.
-
-
Verify and document Codec Set and Encryption details.
The SBC connects to the DMCC Observers over SIP. By default, the following ports are used on the CXone Mpower side:
-
Non-secure (TCP):
-
Observer 1: 5060
-
Observer 2: 5062
-
-
Secure (TLS):
-
Observer 1: 5061
-
Observer 2: 5063
-
-
Define two separate SIP destinations (or IP Groups or Session Recording Servers) that correspond to the two DMCC Observers, including:
-
Observer FQDN or IP
-
Port (5060/5062 or 5061/5063, depending on security)
-
Transport (TCP or TLS)
-
-
For each recording rule or session recording configuration on the SBC:
-
The Recorder, SRS, or Recording Server points to the correct Observer FQDN and port for the relevant telephony system.
-
If you are using secure SIP (TLS), the appropriate TLS context and certificates are configured as described in the SBC sections in this topic.
-
Each DMCC Observer must be resolvable via DNS and must have its own DNS record. Don't reuse the same FQDN for both Observers.
-
Create a DNS record for Observer 1:
-
Type: A or CNAME
-
FQDN: for example,
observer1.<your-domain> -
Target: the Observer 1 IP address.
-
-
Create a DNS record for Observer 2:
-
Type: A or CNAME
-
FQDN: for example,
observer2.<your-domain> -
Target: the Observer 2 IP address.
-
-
If you use AWS Route 53 for DNS, create the corresponding records there.
NiCE Professional Services will reference these FQDNs in the CXone Mpower configuration.
Because you are using two AES servers and two DMCC Observers, the network paths must allow all combinations of Observer AES traffic.
-
From the customer side, configure VPN routing so that:
-
Observer 1 can reach AES A and AES B.
-
Observer 2 can reach AES A and AES B.
-
-
Configure the following firewall rules:
-
Allow inbound and outbound SIP and RTP/SRTP traffic between:
-
Each Observer IP (or subnet used by CXone Mpower).
-
Each AES server IP.
-
-
Open the required DMCC and SIP ports:
-
DMCC ports as configured on AES A and AES B.
-
SIP ports 5060/5062 (non-secure) or 5061/5063 (secure).
-
-
Prepare information for NiCE Professional Services
Before you can begin your CXone Mpower CTI configuration, you require specific information.
Ask the Avaya site engineer to verify the information below is entered in the Excel file. Submit the Excel file to NiCE Professional Services.
When using two DMCC Observers on a single tenant, provide one full set of switch information per telephony system (Telephony System A and Telephony System B).
|
step |
parameter |
Where is this configured? |
|---|---|---|
| 1 | DMCC Multi‑Telephony Support – provide separate switch information for each Avaya telephony system (A and B) | Avaya AES / Communication Manager environment |
| 2 | Avaya DMCC port number: Check the Avaya DMCC port number for a secure connection and an unsecure connection. | On the AES Server. |
| 3 | Verify the DMCC ports are enabled. | On the AES Server. |
| 4 | Verify the Real-Time Third Party Telephony Recording (Multi-ACD) username and password for Avaya DMCC as defined on AES. | On the AES Server. |
|
For Virtual Extensions:
|
||
| 5 | Verify the Avaya DMCC symbolic name. |
On the AES Server. In the Switch Connections area, verify the Connection Name. The Connection Name is also known as the Symbolic Name. |
| 6 | Verify the Observation Code in the Service Observing Listen Only Access Code field. | On the Communication Manager (CM). |
| 7 | Verify the list of supported codecs. | On the Communication Manager (CM), verify the codecs that the organization is using. |
| 8 | Verify the list of supported encryption algorithms (AES_128_ Counter (aes)/ No Encryption / AES_128_ HMAC). If AES_128_ HMAC is supported, the Real-Time Third Party Telephony Recording (Multi-ACD) engineer must be informed whether to use HMAC32 or HMAC80. | On the Communication Manager (CM). |
| The Avaya site engineer must inform the Real-Time Third Party Telephony Recording (Multi-ACD) engineer which encryption is used on site: HMAC32/HMAC80. |