There are many different hostnames and services used by the CXone Mpower platform. The diagrams on this page show the components and encryption used in communicating with each hostname.
Private Data Center Connectivity
This diagram represents how users connect with our application infrastructure in NiCE's US and EU Private Data Centers for CXone Mpower. Users connect with these data centers through our cluster server set, DNS hostnames.
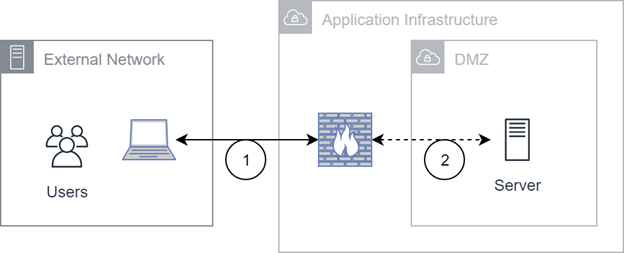
Flows
-
Traffic from the external network ends at a hardware firewall. This terminates the TLS
 Transport Layer Security. A protocol that provides end-to-end security for data sent between applications. session. Unsecure traffic is allowed and handled by the server.
Transport Layer Security. A protocol that provides end-to-end security for data sent between applications. session. Unsecure traffic is allowed and handled by the server. -
Traffic between the firewall and server is not encrypted.
Direct Public Cloud AWS Availability Zone Connectivity
This diagram represents connectivity with our cluster server set, DNS hostnames. Users access our servers through an application load balancer.
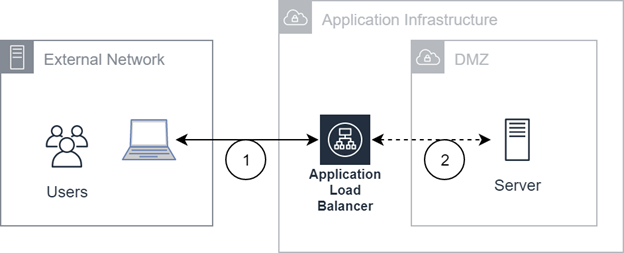
Flows
-
Traffic from the external network ends at an application load balancer. This terminates the TLS
 Transport Layer Security. A protocol that provides end-to-end security for data sent between applications. session. Unsecure traffic is allowed and handled by the server.
Transport Layer Security. A protocol that provides end-to-end security for data sent between applications. session. Unsecure traffic is allowed and handled by the server. -
Traffic between the application load balancer and the server is not encrypted.
Indirect AWS Data Center Connectivity
This diagram represents connectivity between users and our indirect AWS Data Center through the use of hostnames.
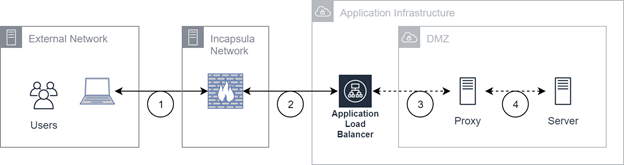
Flows
-
Traffic from the external network ends at an Incapsula service. This terminates the TLS
 Transport Layer Security. A protocol that provides end-to-end security for data sent between applications. session.
Transport Layer Security. A protocol that provides end-to-end security for data sent between applications. session. -
Traffic between the Incapsula service and the application load balancer. A new TLS session starts at the Incapsula service. This TLS session ends at the application load balancer. Unsecure traffic is allowed and handled by the server.
-
Traffic between the application load balancer and the proxy is not encrypted.
-
Traffic between the proxy and the server is not encrypted.

